Mars, Unmasked: RedZone Zapped from Second Life Grid
RedZone goes down in flames, but highlights security and privacy issues that Linden Lab must now work to solve.
RedZone goes down in flames, but highlights security and privacy issues that Linden Lab must now work to solve.
Sometimes, the story goes to press before the real news breaks. That’s what happened last week. A lot has happened since then. I’ll try to catch everyone up and make some sense of it all.
On the evening of Friday March 11, a few hours after I kicked last week’s column upstairs for posting, the server belonging to zFire Xue, the creator of zF Redzone was brought down by a SQL injection attack. This attack was in response to an open challenge that zFire had thrown down, as follows:
Originally Posted by zFire Xue
‘Let me be very clear when I say:
zFire did not ‘underestimate the tech savvy community of Secondlife if he thinks they will not [insert illegal hack attack here”’
My server remains online, DDOS, URL probing, port scans, and seriously did you just try to ‘NUKE’ me on port 139 Mr Germany?
They offer technical resumes, and warnings of everything they feel I did wrong.
My server is still online, even with low tech abuse reports to my ISP, DDOS of 860 million a second (Impressive but pointless), and whatever else.
This therefore means that my server is the most secure server and database in all of Secondlife.
That is a challenge.
Many people have already made battle cries, suggested methods, or claimed not to support methods of hacking.
Bring it on.
I am the guy that logs your shoe size right? Do you think any server software exists that does NOT log the IP, date and time of an attempted cybercrime? Wow this will be fun.
‘My computer is bigger than your computer’
Cyber criminals need banning, so please feed attempts to isellsl.ath.cx’
The question as to whether this was garden variety arrogant idiocy, or a calculated move designed to take his database out, while allowing him to legitimately blame it on someone else (in this case, he would most likely blame his propaganda target of choice, Green Zone, regardless of who actually did it) is up for grabs. Either one is possible.
Either way, the attack not only occurred, but worked quite well. In fact, it is clear now that over the course of the weekend, several attacks were carried out on that server by different individuals or groups.
The first acknowledgement/responsibility claim came over at the no2redzone site, from Security Through Hackscurity and read thusly:
(12:35:24) :
‘we hacked becuse zfire xue challenge hacker to hack. he so script child that it take second. site down. site back. second to access again. site go down come back. again. again. again access until he close hole which place everyone data in secondlife at risk. oh the thing we see lar. admin page with manual copybot name enter and list of added user. not detect by rz! manual! hundred user manual entered! user vasilisa shilova manual enter many name too! database dump say video true. he log wrong entered password. everyone owner redzone need change SL password! how we send database to linden with anonity? we still work on this. we not use or release database. we attach example admin log screen as access prove. we only hack becuse he ask. if he deny hack we post more criminate screen until doubt gone.’ This comment was accompanied by a URL to a screencap posted at tinypic. I’ve reproduced it here just in case that goes poof:
There’s a number of interesting things about this photo, but hold that thought until the end of the recap.
At some point early Saturday morning (March 12), the Alphaville Herald received a package from a person or persons unknown. What it contained were screencaps that seem to prove not only what many people (self included) have been saying all along, but that the video discussed in my last column was indeed legit.
Putting aside my envy that the Herald got all the fun stuff (I kid, I kid), the article is explosive, and well worth a read. The screencaps sent to the Herald indicate that zFire Xue was indeed illicitly harvesting the data (particularly potential passwords) of his own customers. Further, it goes on to show that many of the ‘gridwide copybot bans’ were entered manually, by either zFire or his partner, Vasilisa Shilova (rather showing that they had nothing to do with ‘copybot’ and everything to do with ‘being rid of people we don’t like’), and further lends credence to the video, as there’s a point where the following seems to be said:
‘”A little useful thing, I’m also going to make a display of peoples real world locations for us only, that will be very interesting. Nobody else can access this page at all. Only V and Z”
Two bit or not, that’s a very frightening thing for a lot of people.
Perhaps most upsetting of all, was the indication that zFire’s Prim Animator, which by all accounts is an otherwise excellent product, may be harvesting data also- to a horrifying end. We’ll get there. Hang tight.
The attacks on zFire’s server and database continued throughout the weekend. While many people believed that this was zFire’s golden opportunity to skip out and run, I disagreed and assured everyone that no matter what- he would be back, no matter how long it took.
Sure enough, on Sunday afternoon his site went live again, though it was clear that he had plans to move his forum to another (presumably more secure) location. Bear in mind- everyone who knew anything about computer security that got anywhere near his server or database had already pronounced it completely and utterly insecure. People who insisted otherwise did so out of blind allegiance to zFire- not from any real, informed knowledge. They simply believed what they wanted to believe. In the end, it has been zFire’s own supporters who have gone up in flames here. That being said, if you have ever owned a RedZone product, or in fact ANYTHING ever created by zFire Xue or have ever visited his website for any reason- change your SL password. Right now.
However, as awful as all these things are, they are (believe it or not) only the tip of the proverbial iceberg.
As someone who has used the same internet nickname for over 15 years, I’m going to offer a bit of advice- if you’re only going to use one name, don’t tie it in to anything stupid. To not manage to figure this out is a sign of serious laziness(and a lack of creativity).
However, everything to date about zFire and RedZone has been lazy, lax security on his own server included. Where zFire completely collapsed is his fascination with Mars.
In this case, Mars is not referring to a planet, but to the Roman god of war. Let us review:
The pattern here is clear. Aside from zFire’s fascination with all things Russian (which is fairly obvious in everything he makes), even before the now infamous ‘Mariana’ video came to light, it’s his attachment to the name Mars.
Now, let’s go back to that photo up there- the one the hacker left over at no2redzone. You see that uppermost entry? All those references on that page to KoM? Let’s talk about that.
Back in 2010, a few months before RedZone was invented, zFire had another interest. It was called… the Knights of Mars. This sounds like fun, right? A roleplaying game of some kind, perhaps? Could be cool, if you’re into that kind of thing… right?
Wrong.
Knights of Mars was a ‘bounty for hire’ group in SL, that claimed for a fee (which had to be paid via Paypal only – in other words, in real money, that did not go through Linden Lab’s hands) that it would ‘eliminate’ your enemies from the grid for you, making sure their accounts were deleted.
Let’s see what they have to say for themselves, shall we?
‘As you can see we are true heros of SecondLife. Doing the dirty work that LL is too busy, blind or bureaucratic to do.
If you know just one person that has a very good reason to be dropped from SL, you’ve come to the right place. ‘ Why can these people never use spell check…
Anyway. This site is copied exactly in two locations.
1. Location 1- its own domain, at knightsofmars.com . As of Wednesday, that domain’s ip pointed to….. the same as zFire’s. It has since been moved to another location in the area. The address was anonymized, but was grabbed before that could occur (zFire wasn’t fast enough).
2. Location 2- as a copy (or the original, can’t be sure, but they are identical) directly listed under zFire’s isellsl.ath.cx domain, which finally seems to have gone poof late Thursday night.
Interesting, no? Wait, I’m not done. Let’s look at what the FAQ for the Knights of Mars says:
Have a look at the two bits highlighted in red. So, they know what they’re doing is against TOS (!), and they had plans in April of 2010 to create an anticopybot device.
Anyone want to take a guess at that?
But wait, there’s more!
Let’s recall that RedZone is not ‘just’ an anticopybot device (actually we know it’s not an anticopybot device at all by this point). it’s a security device. Who would need to buy a security device? People being harassed, of course.
You mean… what Knights of Mars was *designed to do* in the first place?
Hm.
But before we move on from the Knights of Mars, let’s have a look at their backstory:
I’ll just leave that one there without comment and back away slowly.
Remember what I said about zFire’s Prim Animation tool? People really love the thing- it seems to be universally heralded as a great device. But check out this closeup of one of the photos that were sent to the Herald:
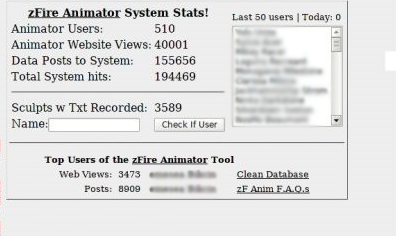
This appears to be indicating the fact that the prim animation tool was being used to datamine also. Well, okay, no one is really surprised about that at this point, are they? But there’s more to it than that. Let’s talk about how Prim Animator works.
Prim Animator allowed the owner to record a frame by frame prim animation sequence (this is not to be confused with mocap, with can create avatar movements). For each frame, all the parameters of the prims you are trying to animate are recorded, along with their linkset UUIDs (the code that identifies each individual object to a Second Life server). When you’re done, you send that information to zFire’s server, which then translates all that information into an lsl (Linden Scripting Language) script, and sends it back to you. You then put this script into your item with a controller script and there you are! Instantly animated stuff.
I have yet to see a person criticize the function of this product. People seem to really love it. Now let’s look a little closer.
As I said, you send all the prim parameters, and the UUID of the linkset to zFire’s server, and it sends you back a script to use in your product.
Here’s some things you should know:
The one thing copybotters cannot steal… is scripts. All one needs to steal an object (without scripts) is the UUID of the object (and its textures).
Now, a word from someone who claims to have cracked zFire’s database:
‘about animater… there is tables with all sculpts and other infos. might be used by zfire or people taking tables. not good’ – rafferten
If what rafferten says is true, it means that (watch this, here’s the punchline) zFire had the means to access, take, and use or resell, anywhere, on any virtual world grid, any object that had ever seen sent to him for a script.
It would be the ultimate copying device.
What better way to capitalize on the fears of copybot than… copying? What way to capitalize on fears of greifing than… griefing?
We have a term for that you know.
Why would anyone want the passwords at all? How does this all tie in to wanting to seek out alts in the first place?
Despite what some may believe, not ‘everyone thinks it’s fun to out alts.’ In fact, most people really and truly do not care which accounts might be alts of anyone else(and if you do I suggest you have too much time on your hands and to take up tennis). But there is a way that the quest for passwords and alts tie together.
How many people use the *same* password for *all* their SL accounts?
Probably? Quite a lot. Let’s face it, most people use a set of several passwords with variations for everything- they simply can’t *remember* more. But one password to access each of your potential SL accounts makes a lot of sense- not from a security perspective, but from a human one.
Cracking one password could potentially crack them all- if you knew which accounts were the correct alts. Even if the device got a ton of false positives- as long as it got *some small number of them right*, it might be useful. Especially if you were looking to steal things to begin with.
And Then Came Monday- the Day Things Got Real
On Monday morning, I had an explosive piece of information dropped in my lap. This same piece of information was confirmed by Theia Magic, who had gotten the information a couple of days earlier but was still sitting on it- she had sent it in to Soft Linden over the weekend.
All this time, I’ve never mentioned zFire’s real name. It’s not that I didn’t have it. I did- I’ve had it for a month now. Everyone and his dog had it. It just wasn’t important, and I didn’t need to use it to tell the story.
It’s important now. zFire Xue’s real name Is Michael (Mike) Stefan Prime. This was determined a month ago- a result of his having publicly listed his company, Insanity Productions, with the BBB, and established a LLC for it (both of which are matters of public record). It was also confirmed by backtracking to his server, which is located in his house.
His name is important now, because there’s something about him you need to know.
What the hell, here’s one more.
Michael Prime (“Prime”) was charged with, and convicted of, one count of conspiracy to commit wire fraud, in violation of 18 U.S.C. 371; one count of conspiracy to manufacture counterfeit securities, in violation of 18 U.S.C. 371; and three counts of possessing, manufacturing, and uttering counterfeit securities, in violation of 18 U.S.C. 513(a)
Fraud (and on ebay no less). In addition, he had previously been convicted for first and second degree theft, as well as two counts of possession of stolen property in the second degree, and forgery, all at the age of 19. But wait? How do we know this is the same Mike Prime? There’s more than one of them in the US, right?
There is. But as I’ve said over and over again, this one is sloppy.
In this case, because of how sloppy this all is, the trail is not only visible, but glowing in bright neon colors. It was laid out by Theia Magic perfectly (I couldn’t have done any better, and she has given me her kind permisssion to post her words here): –zFire has publicly admitted his YouTube account is marskgb006
-In the court documents in question, it names Shawn Cahill as one of the defendants and Mike’s friend:
“The extrinsic evidence included money orders and e-mail correspondence with aliases used to conduct fraudulent transactions, written reports by both the fingerprint and handwriting expert, and certified copies of prior convictions for both Prime and his friend Shawn Cahill”
-On marskgb006 YouTube account, there is this video. Notice the title John vs. Shawn Cahill
-In the court documents in question, it names Juan Ore-Lovera as a co-defendant
-Also on marskgb006 YouTube, there is this video. Notice the title of Juan’s reaction to the ‘John Vs. Shawn Cahill” video:
-Remember the John Hamlin mystery? CEO of Insanity Productions with Mike Prime? Well, here’s Juan’s (the co-defendant in Mike’s criminal case) Facebook. Look who his friend is- John Hamlin. John Hamlin | Facebook
There is no way it’s a coincidence that men who played a part in the criminal trial of Michael Stefen Prime are also in YouTube videos under an account that zFire publicly admits is his.
There’s no “if”. zFire is Michael Stefan Prime. Amazingly, there’s still a couple of True Believers out there, that despite the insane amount of evidence that they’ve been duped by a crook (and not even a good one- I mean one on the level of a bad Batman villain- which may be insulting bad Batman villains), that they keep trying to find ways to dodge the obvious:
They’ve been had. Totally. Completely. The closer you were to this guy and the more you believed and trusted him, the more he ripped you off. He isn’t your buddy, he isn’t your friend, and he doesn’t care about you- and he never did.
I’ll say it again. If you ever had anything at all to do with this guy- ever owned ANYTHING he ever made- change your SL passwords. Right now. Hell, change all of your passwords.
Also on Monday, I was handed a link to a pastebin page containing the results of a port scan done on zFire’s well known domain. If you want to see it yourself, it’s here.
The analysis handed to me of that page read: ‘Looks to me like [zFire” is not dealing with a little hacker problem, he might just have a whole hacking community on his ass. Also looks like he has a lot of open ports on that machine. Very bad for a server to respond to a port scan like that. The pastebin info was submitted on Feb 24th before his invitation [to attack his server” as well.’
So much for his boasting of a secure system.
On Tuesday evening, an interview with zFire was posted in the Alphaville Herald. zFire admits to having his system cracked, and is not the happiest of campers throughout(though at least for one reason, I don’t blame him). The interview is nasty all the way around, but well worth a read, and I encourage people to check it out. However, tucked into the middle, was this exchange:
Pixeleen Mistral: Are you concerned that today’s developments might lead to your accounts being banned?
zFire Xue: Nope. Linden Labs knows fact from fiction. WIthin two hours, zFire had disappeared from the grid.
It wasn’t just him. zFire, all his known alts (and some that probably none of us knew), his partner, his partner’s alts, their groups (including the one I posted last week), the working scripts in the RedZone devices, their mainstore, *and their land* were seized by Linden Lab. It was as clean a sweep as one could imagine.
Though I was not present at the location, a large crowd gathered to watch this happen (there have been plenty of photos). Soft Linden removed the RedZone mainstore personally(and I assume everything else as well).
On Wednesday night, long after office hours, there was a FULL rolling restart of the *entire* Second Life grid, which was not a scheduled maintenance. It is widely believed the purpose of the restart was to clear away the last working vestiges of RedZone from the grid.
As I said many weeks ago and have been saying ever since- this particular device, while making for an interesting story and a focal point for people to learn about security and privacy concerns within Second Life, is not the cause of these issues. It is merely a symptom.
At this point, as the Lab moves ever closer to further integration with larger, more open social networks, these problems will only become larger. In reality they should have been dealt with years ago.
As a technical matter, there is no device that will be effective against copybot. If you can view something in Second Life with your viewer- you have *already copied the information*. The only difference is extracting it in a usable form on the other side.
In terms of security, the debate rages as to whether or not IP is a) even remotely effective, b) if so, for how long, and c) should that power be given to residents at all. Feel free to add your own view in comments on that one.
the dialog has started, and is continuing. Linden Lab needs to be a part of that dialog as well, in order to serve the needs of their userbase and to prevent things like what happened here from happening once again (or continuing to happen with other products that are still on the grid).
The privacy and security discussion goes on, and hopefully what Rod Humble (CEO of Linden Lab) will live up to his statements on the protection of privacy.
Fortunately, now, without RedZone in the way.