Previously, on British Outfitters…
Lisa Hughes, a New York-based content marketer for UK apparel company British Outfitters, just learned that someone has hacked into her work email to steal ideas for an upcoming marketing campaign.
The new campaign, aimed at resurrecting British Outfitters’ tainted image, was centered around an Instagram video contest that would connect user-generated content with the company’s new TV ads.
Days before the campaign launch date Lisa received the news that a major competitor, American Denim, was launching an identical campaign led by her ex-boss, Don Makerfield. After looking into possible leaks, her IT team informs her that her email account was hacked. Coincidence?
Join us as we wrap up this five-part series on Conquering Content Marketing.
Did you miss the previous installments and want to catch up now? See:
Hacked!
“It appears that you’ve been hacked. The log files show activity from outside the country accessing your email.” Frank’s words made Lisa’s stomach drop.
“What do I do?” she asked.
“Well,” said Frank, “we’ve reset your password and blocked those IP addresses from our network. We’re going to continue investigating, but your account should be safe now.”
“Safe from what?” she thought. AD (American Denim) already stole her campaign idea and beat them to market. She was upset. Upset at IT for not keeping her email secure. Upset at herself for not launching the campaign sooner. But mostly upset at Don for being so underhanded.
It’s one thing to create a PR nightmare before leaving, but now to actually hack into her email to steal her ideas and pass them off as his own? Who does that?
Frank sat in uncomfortable silence while Lisa processed everything.
“Thanks, Frank. Let me know what else you find out, and can you drop a hard copy of the incident report on my desk? I want to keep it for my records,” Lisa said as she shot up and burst through the halls. She was late for her own team meeting at 3:00. Just a few hours early she ordered the team to go live with the campaign ahead of schedule, and that was all happening right now!
Launch
Lisa walked into the conference room hoping to hear good news from the team.
“Kelly, how’s the website coming along?”
Kelly was happy to report, “The contest is live on the site, and the email blast was sent to our customer list.” This was encouraging, the first piece of good news Lisa heard all day. It was time to activate her distribution strategy.
“Seth, head over to the social group and make sure they’ve announced the campaign is live. I’d like them to share the best submitted images and video every 15 minutes or so, and I want to see all the metrics: likes, retweets, favorites, clicks, increase in followers, referral traffic, sales – everything!” She was just getting started.
“Kelly, reach out to the mommy bloggers I met with a few months back. I’ve got three email lists saved as ‘Influencers’, ‘Top Influencers’ and ‘Journalists’. Send all three lists the contest promo email. For the ‘Top Influencers’ include a promo code for a free pair of jeans. Wait 24 hours, then pull a report of everyone who submitted an entry to the contest so far, and get that to Facebook and Twitter to generate a look-a-like list. Shift 80 percent of the advertising spend to that list, and leave the rest of the budget for the campaign’s general target group. I have something else planned, but I need to meet with PR first.”
And with that she took off down the hall.
The Leak
Lisa knocked politely on the head of PR’s office door frame before slowly entering.
“You have a second, Tim?” she asked.
“Sure, have a seat.”
Lisa cut right to the chase, “You know my email got hacked, right? And that’s how Don found out about our campaign.”
“Yeah, I heard a few people talking about it outside my office earlier.”
“Well, apparently they’re not the only ones talking about it. Someone here leaked it to a journalist, and now I’m being asked for a comment on an article they’re writing about it.”
“Oh wow.” Tim was shocked that word had spread so quickly. “Forward any emails or calls you get to my office, and I’ll handle it.”
“What will happen to the person who leaked the info?” Lisa asked.
“I don’t know. It’s really hard to track down who it was unless they used their company email or phone. I’ll have Frank run a check on the network to look for strange outgoing calls or emails. I’ll let you know if anything turns up.”
That was all Lisa needed to hear. “OK, thanks so much Tim. I’m starving, gonna grab a late lunch.”
Lisa swung by her office to pick up some papers and walked to her car. She drove a few minutes down the road to a Wendy’s, and as she was waiting for her order she got on her phone and registered an anonymous Gmail account. From there she emailed the journalist a copy of her campaign email, Don’s campaign email, and Frank’s incident report, which contained details of the hack.
DOS?
It was 5 a.m., and Frank’s phone would not stop vibrating. “Who could be calling at this hour?” he growled. He finally rolled over and peeled open an eyelid to check his phone. A custom hosting app that alerts the team when there is trouble with a server was making all the noise.
Opening the app, he saw the servers powering British Outfitters’ website had been overwhelmed with activity for hours. This was not normal. “Maybe it’s a Denial of Service (DOS) attack?” he thought, as he jumped up out of bed. “I’d better get to the office.”
Lisa arrived at the office around 7 o’clock, surprised to find Frank’s car in the lot.
Inside the office she stopped by Frank’s desk to comment on his early arrival. Before she could even say, “Good morning” Frank blurted out, “Lisa, you won’t believe this. The site is getting slammed with visitors. I thought it was an attack, but as far as I can tell it is real traffic. It’s coming from a ton of blogs and social sites.”
“Uh oh,” Lisa thought.
30-Second Commercial Break
Let’s take a step out of our story for a moment to consider how the concept of measurement plays into content marketing.

Since the beginning of our story, we’ve seen a variety of marketing tactics ranging from banner ads to viral videos to offline billboards.
British Outfitters saw a massive spike in traffic and sales when the company made news headlines, regardless of whether it was good or bad publicity. This informed Lisa’s strategy of turning the hacking scandal into news which created exposure for her marketing campaign and drive hordes of traffic to the company’s website.
But what worked for Lisa won’t necessarily work for you. There is no silver bullet when it comes to marketing. You have to experiment to find out what works, and it starts with tracking.
And most marketers DO have tracking in place. According to Marketing Sherpa’s 2013 analytics research, 96 percent of markets have analytics data setup on their campaigns.
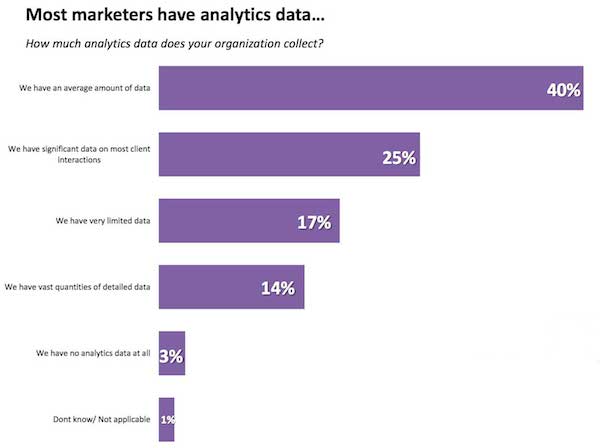
But they’re spending the majority of their time fiddling with reporting instead of actually extracting insights and testing their hypotheses.
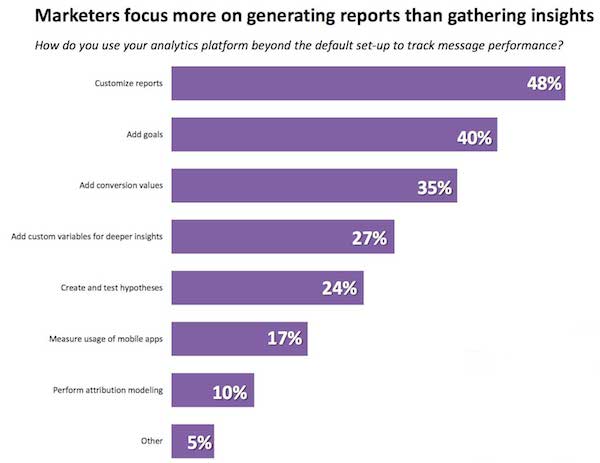
A great CMO once told me, “If you can’t track it, it’s not worth doing it.” Great advice, but you can’t just generate reports and call it a day. Go the extra step mile, and convert the data into learnings that can be applied to your next campaign.
Now back to our story…
The Conclusion
It was Lisa’s second night in London, and her body was still jet-lagged from the flight. Tomorrow morning was the big meeting with her boss, Holly Spaulding, and several other VPs to discuss her three-month-long Instagram campaign that wrapped up last week.
She popped a sleeping pill 20 minutes ago, but her mind was still wide awake. She knew there would be a lot of questions about the campaign, so she rehearsed them in her head.
“What were the results of the campaign?”
“The campaign was mentioned on almost 200 blogs and news sites, and received thousands of mentions on social networks. The campaign received 1,800 videos submissions. Total incremental traffic was 85,000 visits which led to an 18% increase in total sales.
“What happened to American Denim’s competing campaign?”
Once the story broke about how American Denim hacked into my email to copy our campaign strategy, there was a strong media backlash again the company. Over the next few weeks their campaign fell apart.
“Was Don Makerfield behind the hacking?”
Surprisingly, no. Apparently Don was brought on to execute the campaign, and didn’t know about the hacking until the media covered it. Somehow, he discovered several upper managers at AD were involved in the hacking, and ended up blowing the whistle on everyone. I don’t know if he’s still at the company or not, but several VPs resigned shortly after.
Lisa was starting to feel the sleeping pill kick in. She closed her eyes and hoped someone in tomorrow’s meeting would ask the question she had a killer answer for:
“What do you have lined up for your next marketing campaign?”


